
HIPAA Compliance Roadmap
Overview: With the Public Health Emergency (PHE) coming to an end in May 2023, many medical and mental health providers are looking for a shortcut or template for HIPAA-compliance. Sadly, we have bad news on that front, but also good news, some solutions. Unfortunately, there is no “one-size-fits-all” for digital security and HIPAA-compliance. In addition, HIPAA has been updated with HITECH laws, and other clarifications, which added more definition, requirements, and significant fines. HIPAA is a digital security framework for medical and mental health providers, health insurers and related fields.
The BAD NEWS is that there are no HIPAA-compliance shortcuts and some “HIPAA-Compliant” software is deceptive and risky. (But there some short term solutions). Most software websites overstate (shocker), or misunderstand HIPAA-compliance, placing your organization, your license, and your patients at risk. “HIPAA-compliant” software and/or your IT department alone cannot make you HIPAA-compliant. You, as a medical or mental health professional, have requirements that software and your IT department cannot do for you. It’s time to become educated on the responsibilities that you will need to understand and perform no matter what vendor is selected, even if you have an IT department.
HIPAA-Compliant Software Does Not Meet All HIPAA Requirements. HIPAA must be applied to organizations individually, and learned by all staff with access to any type of patient information. Software and automation can do portions of this, but a significant amount is still in your hands.To be fair, maybe your current “HIPAA-compliant” software asked you the roughly 770 risk assessment (required) questions and filled out the required 10 documents for you. No?
It’s time to protect your patient’s from losing their legal right to privacy from hacking or accidental staff exposure. Protect your practice from costly and frivolous lawsuits, threats to your license, fines, damage to your reputation with patients, professionals and referral sources, and protect your ability to work.
The GOOD NEWS, we have solutions in this article and our consultants can help and do most of the policy/procedure development and education for you. If you are concerned about your software vendor, we can provide software guidance, short and long term solutions, AND we can work with you in a consultant role to help you go through the processes and paperwork that only humans can do. Once you understand HIPAA concepts and have your administrative policies and procedures in place, you can maintain that with the help of certain HIPAA-secure software. We’ll first explain why some “HIPAA-Compliant” software is deceptive, risky, and NOT HIPAA-Compliant, then provide the roadmap for becoming truly HIPAA-compliant.
Why You Need More Than A BAA and Encryption: The amount and type of HIPAA protections required for a company is ALWAYS dependent on the complexity of the organization and how one handles Protected Health Information (PHI). First, it is important to know that there are 18 types of PHI. You are required by HIPAA to do a Risk Assessment, which is an accounting of where PHI exists and how it is protected at all times. You may be surprised by your company’s leakage and vulnerabilities, even when you use software labeled “HIPAA Compliant.” HIPAA compliance begins with a risk assessment process and is maintained by administrative policies and procedures, technological safeguards, physical security, and regular reviews and updates. HIPAA-compliance requirements vary across all organizations because each organization has different workflows, data, software, culture and staff. Each company needs to go through the process of evaluating current administrative, technical, and physical security measures and privacy policies using HIPAA-HITECH standards. Then examples of additional required activities include: make plans for remediation, begin remediation, audit again after remediation, and create the required documentation (10 of them) of compliance measures. In addition, staff need to document annual training on HIPAA requirements and have documented updates throughout the year. The organization also needs to have documented roles and responsibilities (including but not limited to a Privacy Officer), all of which are necessary to maintain compliance long term. This should be updated each time there is a change and reviewed formally at least once per year (See graph). We can guide you through this process and tell you quickly what different technical terms mean, what applies to you, what procedures would create compliance, how to document compliance, and train your staff to perpetuate compliance to digital security long term.
Can You Tell HIPAA-Hype From HIPAA-Compliance?: Unfortunately, it can be difficult to discern HIPAA-Hype from HIPAA-security and software alone will not be enough, ever. (Never-ever.) An impressive-looking “HIPAA seal” on a website does NOT mean the software is HIPAA-compliant. In truth, there is no official HIPAA government seal. There is no official governmental HIPAA certification for software. The HIPAA-compliant seal most likely means the vendor has some protections that meet HIPAA requirements, like encryption. But the fine print in most of the terms of use may absolve the software vendor of the responsibility of protecting the data (that you were counting on). Some of this is the corporate lawyers hedging liability, which is not always a bad thing. To be fair, it may be just ignorance on the part of the vendor who simply sees a new market for software.
Technically, no software is ABLE to be HIPAA-compliant. There are two main reasons, one legal and one practical. The legal reason is because software is not a Covered Entity, an entity for which the laws apply. Second, and possibly as or more important, at least 20 HIPAA requirements require human interaction and cannot be automated we’ve tried). It is IMPOSSIBLE for a software vendor to know all of your vulnerabilities without understanding your company, your workflows, and performing a risk assessment. Even when a software vendor knows the risks, the software cannot do the human parts of the HIPAA requirements.
Why Do Software Vendors State “HIPAA-Compliant” When They Are Not? To be fair to the software vendors, they state this because that is what is Googled by those who are shopping. Remember that when you pick “HIPAA-compliant software” you are delegating some of your legal and ethical responsibilities to that vendor. Even when the vendor signs a Business Associate Agreement (required by HIPAA), you are also still accountable for that vendor’s use/misuse of Protected Health Information. So be wary of vendors who overpromise and say they cover everything because it technically cannot be true.*
Selecting a Software Vendor: Legitimate vendors will have additional language somewhere on their website regarding the limits of the “HIPAA-Compliant” claim. We helped write the National Telehealth Resource Centers’ guidance for selecting a “HIPAA-Compliant” software vendor. You can select by criteria in the vendor-neutral site TelementalHealthComparisons.com. We also have a preferred vendor who can provide short term and long term solutions AdaptiveTelehealth.com. But remember, even after you select software, digital security is a mindset and a set of human habits that require training, assessment, monitoring, auditing, and coordination between the staff and the software.
Now that you understand some of the issues and the need for more education, policies and procedures, you may feel overwhelmed. You’re normal. That is where we can help.
HIPAA Compliance Solutions
We provide quick and comprehensive consulting and technical HIPAA-Compliance solutions. Contact Behavioral Health Innovation for consulting and training in HIPAA-compliance for your organization.
AdaptiveTelehealth.com is our technical solutions partner. They have approximately 200 modular, white-label options for HIPAA-secure services that can be customized and implemented quickly.
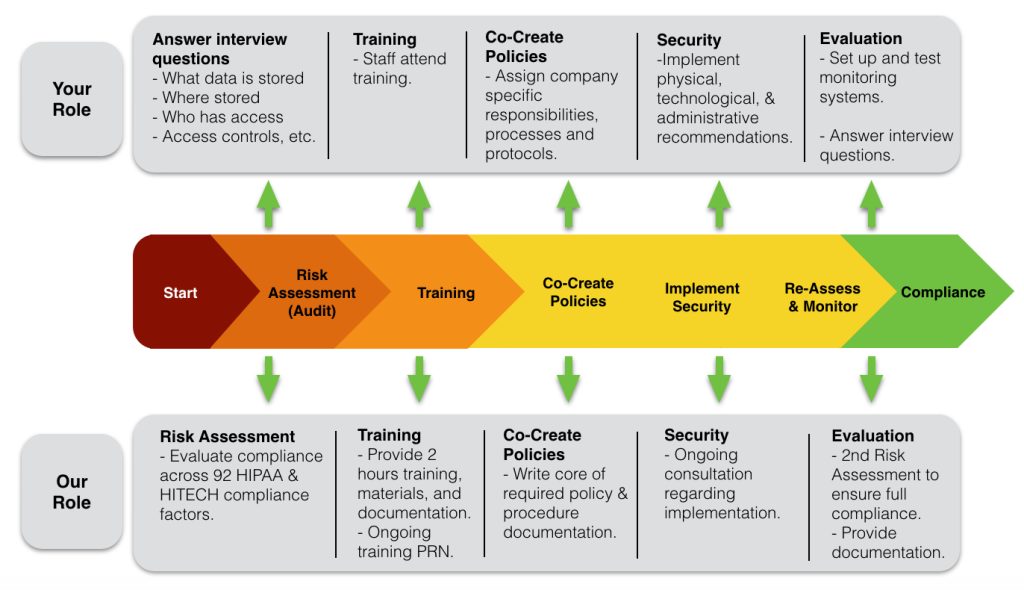
HIPAA-Compliance Roadmap
Since HIPAA-compliance includes several steps, we propose a roadmap to achieve compliance.
- Educate staff regarding HIPAA-HITECH compliance. Provide documentation of HIPAA compliance training for each participant.
- Perform a Risk Assessment in which you document where PHI resides, who has access, how it is accessed, how it is protected, etc. Physical Safeguards, Technical Safeguards, Administrative Safeguards.
- Make a remediation plan to improve protections per HIPAA-HITECH standards.
- Write policies and procedures to document HIPAA-HITECH compliance.
- Obtain Business Associate Agreements for each contractor who has the opportunity to access Protected Health Information.
- Re-Assess – Perform a second Risk Assessment to confirm HIPAA-HITECH compliance after privacy, security policies and protocols have been implemented.
- Monitor HIPAA compliance measures and update policies and procedures to continue to comply as technology and workflows change.
- Limit user access to PHI and require authorized access. (Minimal Use policy).
- Provide a system with secure communication. Clinical services should only be administered when privacy is assured for both parties (Liu et al., 2019).
- System monitoring for secure communication should be implemented to ensure the confidentiality, integrity, and availability of all e-PHI they create, receive, maintain or transmit (HHS, Office for Civil Rights, 2020).
- Design a checklist for the 18 PHI Identifiers to maintain HIPAA Privacy Rule compliance and to identify if e-PHI is exposed to users without authorization.
Utilize the SRA Toolkit for creative workflows that define security risks and build detailed reports for system vulnerabilities and risks. Spoiler alert, there are approx 777 technical questions across 7 tabs.
Documentation Required and Recommended:
- Training documentation (Required by HHS)
- Risk Assessment (Required by HHS)
- Remediation recommendations (Recommended by HHS)
- Risk Management Plan (Required by HHS)
- Logs: Access management, equipment, network, applications (Required by HHS)
- Breach Notification Plan (Required by HHS)
- Policies and procedures (Required by HHS)
- Business Associate Agreement (Required by HHS)
- Business Associate Agreement tracking (Required by HHS)
- Privacy Breach log (Required by HHS)
- Breach Notification Plan (Required by HHS)
- Final HIPAA-HITECH Audit Report (Recommended)
When you work with Behavioral Health Consultants, we fill in these forms for you and help you create the policies and procedures to support HIPAA compliance for the long term.
This has been a summary of the complex HIPAA regulations. It is the professional’s responsibility to read the materials from Health and Human Services regarding HIPAA-HITECH and make application determinations.
HIPAA Compliance Solutions

We provide quick and comprehensive consulting and technical HIPAA-Compliance solutions. Contact Behavioral Health Innovation for consulting and training in HIPAA-compliance for your organization.

AdaptiveTelehealth.com is our technical solutions partner. They have approximately 200 modular, white-label options for HIPAA-secure services that can be customized and implemented quickly.
References:
Liu, X., Sutton, P., McKenna, R., Sinanan, M., Fellner, B., Leu, M., & Ewell, C. (2019, January). Evaluation of Secure Messaging Applications for a Health Care System: A Case Study.Retrieved September 25, 2020, from https://www.ncbi.nlm.nih.gov/pmc/articles/PMC6393161/
Secretary, H., & (OCR), O. (2020, September 23). The Security Rule. Retrieved September 25, 2020, from https://www.hhs.gov/hipaa/for-professionals/security/index.html
Secretary, H., & (OCR), O. (2013, July 26). Summary of the HIPAA Security Rule. Retrieved September 25, 2020, from https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html. Ensure the confidentiality, integrity, and availability of all e-PHI they create, receive, maintain or transmit.
*On a side note, we are not against software vendors, we’re against the deceptive overstatements and promises some vendors make about HIPAA that put patients at risk of disclosure of their private information, and medical and mental providers in legal and moral jeopardy. Several well known brand names have already been caught selling patient information to Facebook and other companies, WHILE claiming to be ‘HIPAA-compliant.” Since the profit for some popular companies is higher than the fines, this will likely continue. So it is important to be a savvy shopper.